Migrating firewalls could be a advanced enterprise, usually involving intricate insurance policies, vital purposes, and the necessity for seamless transition. This publish distills key insights from skilled architects on greatest practices for any firewall migration, after which dives into the distinctive concerns when transferring from Palo Alto Networks to Cisco Subsequent-Technology Firewalls.
Part 0: The Background
Buyer management has determined emigrate from PAN to Cisco. This was a enterprise resolution based mostly on elevated costs by PAN. Not like many firewall migration tasks CX helps, this engagement had the next complicating components:
- Lack of current-state documentation.
- Lack of knowledge of present id answer. Extra particularly, we recognized (with effort) that there was a have to make Cisco & PAN co-exist due to many cases of identity-based firewall enforcement.
- Lack of knowledge of firewall historical past (i.e. WHY is there a firewall right here/what community segments want isolation).
- Lack of knowledge/documentation of applications-and how/the place the firewall coverage helps the purposes.
- 24/7 setting: There isn’t a ‘after-hours’ so each migration effort required vital planning.
Part 1: Common Firewall Migration Finest Practices
A profitable firewall migration hinges on meticulous planning, thorough execution, and diligent post-migration actions. There isn’t a device that may change good practices and this part’s intent is to organize an engineer with expertise required to save lots of one’s sanity:
1. Complete Prep Work:
- Pre-migration Cleanup & Optimization: Earlier than you even take into consideration transferring, clear up your present firewall. This contains analyzing rule and NAT hit-counts to establish unused or redundant insurance policies, and performing object de-duplication to streamline configurations. Would you progress homes with out first decluttering and throwing away trash? If not, why would you progress stale or irrelevant firewall coverage? greatest observe is to make this one thing the client is chargeable for. Like transferring, you’ll be able to’t declutter indefinitely, so guarantee there’s a timeline to which the client is held accountable to.
- Change Administration: Ideally, implement a configuration freeze on the supply firewall. If not attainable, set up strong change monitoring to copy any new guidelines or modifications throughout each the previous and new firewalls.
- Stakeholder Engagement: Determine all mission-critical purposes and their key stakeholders. Their enter is essential for understanding visitors flows and validating post-migration performance.
- Documentation is King:
- Develop an in depth Technique of Process (MOP): Define each step, together with whether or not you’ll carry out a ‘arduous’ cutover or an incremental/phased migration. Embrace clear time targets.
- Conduct Peer Critiques: Have a number of eyes in your MOP and configurations.
- Create a Thorough Check Plan: This isn’t nearly testing purposes; it’s about testing your check plan itself. Guarantee it covers all vital functionalities and edge instances.
- Design a Rollback Plan: All the time have a transparent technique to revert to the earlier state if points come up.
2. Flawless Migration Execution:
- Conduct a ‘Dry-Run’: If attainable, simulate the migration in a check setting to establish potential points earlier than the precise cutover.
- Validate ARP Tables: Test ARP tables each earlier than and after the migration to make sure correct community connectivity.
- Optimize Essential Visitors: Develop pre-filters or ‘fastpath’ guidelines for vital purposes to make sure their efficiency isn’t impacted.
- Pre-stage Monitoring Instruments: Put together customized searches and packet captures prematurely to shortly diagnose points in the course of the migration.
- On-Name Assist: Have software testers and house owners available or on a devoted name in the course of the migration window. Vital be aware: These MAY NOT be the identical individuals. Usually, we got testers, who lacked any understanding of how the applying labored. Guarantee it’s nicely documented the place this expertise lives. Supply/vacation spot IPs & L4 ports-who is aware of these low-level particulars?
3. Submit-Migration Actions for Stability & Optimization:
- Evaluation Submit-Migration Reviews: Completely analyze any reviews generated by migration instruments to establish and tackle lingering points.
- Replace Documentation: Guarantee all community diagrams, coverage paperwork, and operational procedures are up to date to replicate the brand new firewall configuration.
- Steady Monitoring: Implement strong monitoring to trace efficiency, safety occasions, and potential anomalies.
- Coaching and Assist: Educate your operations crew on the brand new platform and its administration.
- Ongoing Optimization: Firewall insurance policies should not static. Usually overview and optimize guidelines to take care of effectivity and safety posture.
Finish-to-Finish Migration Process (Common Steps):
- Obtain and launch the migration device.
- Export the supply firewall’s configuration file.
- Evaluation the pre-migration report.
- Map interfaces, safety zones, and interface teams.
- Map configurations with purposes.
- Specify vacation spot parameters and choose options for migration.
- Optimize, overview, and validate the migrated configuration.
- Push the migrated configuration to the brand new firewall’s administration middle (e.g., FMC).
- Deploy the configuration to the firewall.
- Obtain and overview the post-migration report.
- Configure any extra handbook gadgets.
Part 2: Key Variations and Migration Methods from Palo Alto to Cisco Subsequent-Technology Firewalls
Migrating from Palo Alto Networks to Cisco Safe Firewall brings its personal set of nuances, significantly regarding id integration, coverage conversion, and platform-specific capabilities.
- Identification Coexistence Throughout Migration:
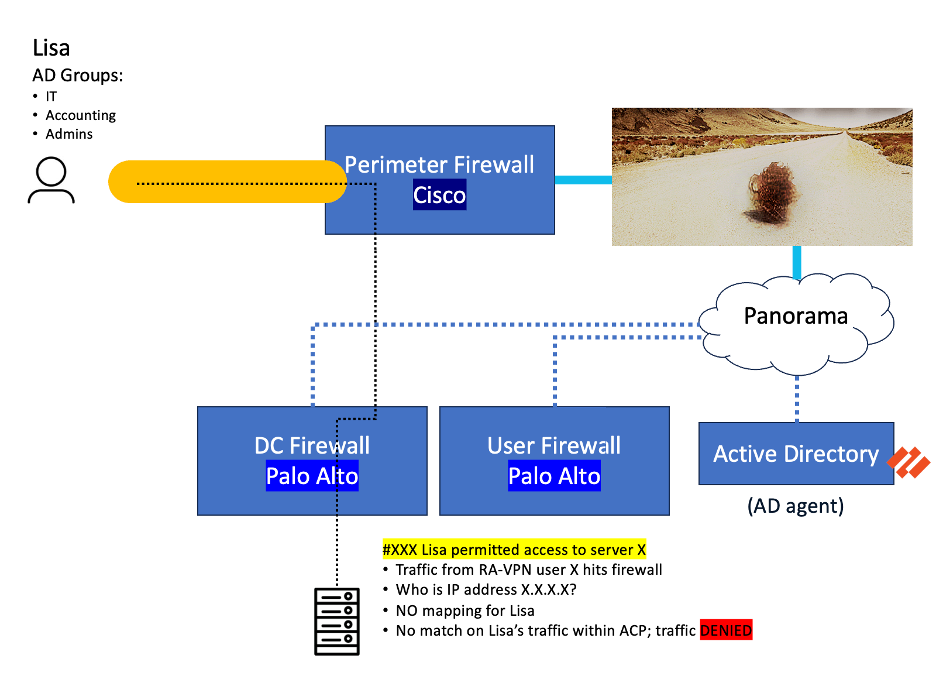
A big problem is guaranteeing consumer id mappings (e.g., “Lisa is 10.14.10.7”) are constant throughout each Palo Alto and Cisco firewalls in the course of the interim migration interval.
- The Drawback: Cisco wants to pay attention to user-to-IP mappings that Palo Alto’s Consumer-ID brokers or VPN gateways already know. With out this, visitors from recognized customers may be denied by the Cisco firewall as a result of it lacks the mandatory context.
- Options Explored:
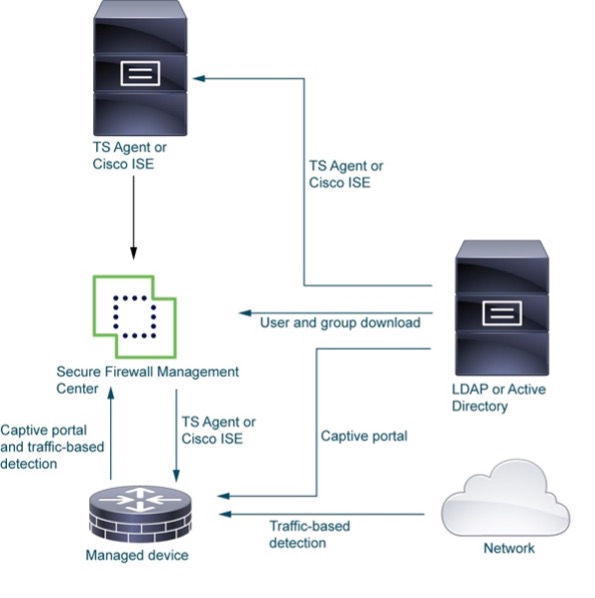
- Devoted ISE-PIC Deployment: Whereas tried, utilizing an present ISE deployment for this objective may be problematic, particularly since PassiveID is incompatible with 802.1x Machine Authentication. Be aware: ISE-PIC has reached Finish-of-Life.
- Syslog Forwarding: A viable technique entails configuring the Palo Alto VPN firewall to ahead Syslog messages containing user-to-IP mappings to Cisco ISE.
- Energetic Listing Brokers: Deploying brokers on Energetic Listing servers or terminal servers can assist each platforms collect id data.
By together with a mixture of syslog forwarding on the PAN VPN firewall and new Cisco brokers on the client AD servers, we had been capable of migrate a downstream PAN firewall to Cisco.
Ought to customers be coming from on-premise (passive authentication) or through remote-access VPN, the Cisco firewall could have a user->IP mapping to verify the suitable firewall coverage is being matched.
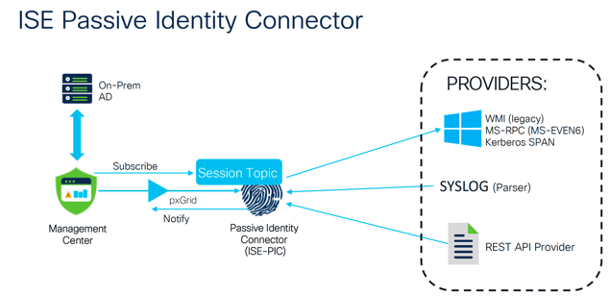

As of Firewall Administration Heart 7.6, the passive ID performance is on the market immediately with out the necessity for ISE-PIC (which went EOL on 5/5/2025).

2. Coverage Conversion with the Safe Firewall Migration Device:
The Cisco Safe Firewall migration device is designed to help with this transition, however understanding its capabilities and limitations is essential.
-
- Extraction & Mixture: The device can extract and mix Palo Alto configurations, figuring out parts like Entry Management guidelines, Community/Port objects, Interfaces, Routes, and Purposes.
- Characteristic Choice: You may choose which parts of the configuration (e.g., Interfaces, Routes, Entry Management) emigrate.
- Software Mapping: It’s essential to resolve any clean or invalid software mappings. In some instances, you may want so as to add port-based equivalents if a direct software mapping isn’t accessible. Assets like Cisco AppID and Palo Alto’s Applipedia can assist.
- Bulk Actions & Optimization: The device facilitates bulk actions and permits for ACL optimization, however bear in mind to pre-stage File and IPS insurance policies within the Cisco Firepower Administration Heart (FMC).
 3. Palo Alto Configuration Limitations for Migration:
3. Palo Alto Configuration Limitations for Migration:
-
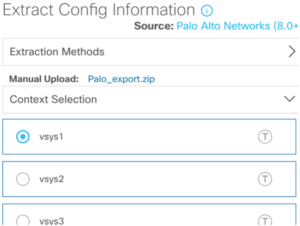
- PAN-OS Model: The supply Palo Alto firewall have to be working PAN-OS software program model 8.0 or increased for the migration device to perform appropriately.
- VSYS Migration: The device helps migration of both single or multi-vsys configurations, that are sometimes merged with VRFs to realize segmentation in Cisco FTD.
- System Configuration: Essential system configurations, equivalent to Platform Insurance policies (e.g., NTP, SSH entry) in FTD, are usually not migrated by the device and require handbook setup.
4. Particular Challenges and Guide Configurations:
A number of parts require handbook consideration or have totally different implementations between the 2 platforms:
- NAT IP and Port Oversubscription: Palo Alto can deal with increased ranges of NAT oversubscription (e.g., 1x, 2x, 4x, 8x reuse of identical tackle/port). When migrating to Cisco, you usually want to extend the PAT pool measurement to accommodate this.
- URL Wildcards: Palo Alto makes use of characters like * or ^ for URL wildcards, whereas Cisco sometimes helps substring matching (e.g., cisco.com as an alternative of *.cisco.com). These want adjustment.
- Nested Object Teams: Community and port object teams nested deeper than 10 ranges should not supported in Cisco FMC and can want flattening.
- Identification Realm/Energetic Listing Integration: Whereas newer variations of the migration device (FMT 7.7+) assist AD/Realm integration, you’ll usually have to manually add id to relevant guidelines and pre-stage the Realm and AD configurations within the FMC.
- NAT Supply Substitute: Manually change NAT supply in Entry Management Coverage (ACP) guidelines with the NAT vacation spot (i.e., swap the translated tackle with the unique vacation spot).
- Unmigrated Objects Requiring Guide Configuration:
- Time-based entry management guidelines. Cisco doesn’t at the moment assist time-based entry management guidelines.
- Identification-based entry management guidelines: You’ll have to explicitly affiliate id teams or particular person identities.
- FQDN objects: Particularly these beginning with or containing particular characters. Wildcard FQDNs usually want substitute or updates.
- URL Filtering Insurance policies: Add the respective classes as insurance policies utilizing URL filtering may not translate immediately.
- Software Mapping: If a rule in Palo Alto used “software default” for service, it can probably be migrated as “any” service in Cisco, requiring handbook refinement. In some case we added port-based equivalents.
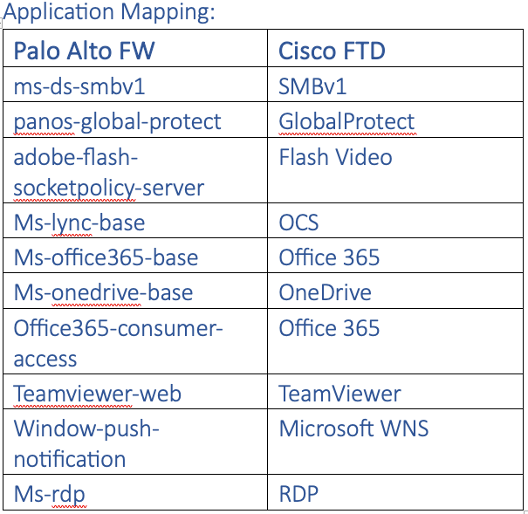

-
- Negate Guidelines: Palo Alto’s “enable X however exclude Y” logic must be translated into express “deny” guidelines in FTD. Cisco doesn’t at the moment assist negate guidelines. This was achieved by merely implementing a ‘deny’ rule in FTD.
- Dynamic Routing: Requires handbook configuration. This is not going to be ported through the migration device.
- Route Reflector: Add FTD as an eBGP peer manually. Extra particularly, cisco doesn’t at the moment (as of this weblog posting) assist iBGP route reflector configuration. This was overcome by manually configuring a brand new eBGP autonomous quantity for the firewall. This additionally required the extra configuration of ‘allow-as in’ as there have been cases the place route propagation hair pinned the firewall.
5. Partially Supported, Ignored, or Disabled Objects:
Remember that sure configurations should not totally supported or are ignored throughout migration:
- Administration Settings (like NTP, SSH entry).
- Syslog Dynamic Routing.
- Service Insurance policies (these usually translate to FlexConfig in FTD).
- Distant-Entry VPN reserved IP addresses (require workarounds through ISE or AD).
- Gadget-Particular Website-to-Website VPN configurations.
- Connection log settings.
By adhering to basic greatest practices and understanding these particular variations when migrating from Palo Alto to Cisco Subsequent-Technology Firewalls, organizations can obtain a smoother, safer, and environment friendly transition.

